Businesses have lost productivity and millions of dollars for not having a secure network. Organisations are using a variety of security products to keep their data secure such as scanners to conduct vulnerability assessment, and intrusion detection systems are available for businesses to use to protect their internet from attackers. Although all these tools serve a purpose in protecting the internet.
In the sections below we would discuss on Firewalls.
Let’s Start!!!
- A firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.
- A network firewall is similar to fencing in building construction, because in both cases they are intended to isolate one “network” or “compartment” from another.
Why do you need firewall?
A firewall works as a barrier, or a shield, between your PC and cyber space. When you are connected to the Internet, you are constantly sending and receiving information in small units called packets. The firewall filters these packets to see if they meet certain criteria set by a series of rules, and thereafter blocks or allows the data. This way, hackers cannot get inside and steal information such as bank account numbers and passwords from you.
Firewall Policies
- To protect private networks and individual machines from the dangers of the greater Internet, a firewall can be employed to filter incoming or outgoing traffic based on a predefined set of rules called firewall policies.
Policy Actions
Packets flowing through a firewall can have one of three outcomes:
- Accepted: Permitted through the firewall.
- Dropped: Not allowed through with no indication of failure.
- Rejected: Not allowed through, accompanied by an attempt to inform the source that the packet was rejected.
Firewall Types
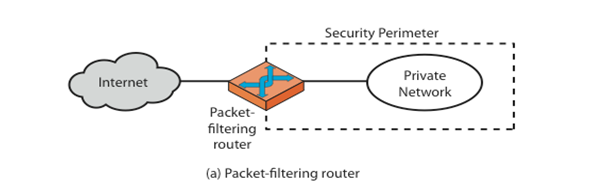
1. Network layer or packet filters
Network layer firewalls, also called packet filters, operate at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set.
Network layer firewalls generally fall into two sub categories:
- Stateful firewalls maintain context about active sessions, and use that “state information” to speed packet processing. Here they make use of State Table.
- Stateless firewalls require less memory, and can be faster for simple filters that require less time to filter than to look up a session. They may also be necessary for filtering stateless network protocols that have no concept of a session.
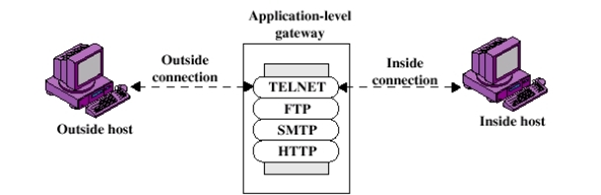
2. Application-layer
Application-layer firewalls work on the application level of the TCP/IP stack (i.e., all browser traffic, or all telnet or ftp traffic), and may intercept all packets travelling to or from an application. They block other packets (usually dropping them without acknowledgment to the sender).
Application firewalls function by determining whether a process should accept any given connection. Application firewalls work much like a packet filter but application filters apply filtering rules (allow/block) on a per process basis instead of filtering connections on a per port basis.
3. Proxies
A proxy server may act as a firewall by responding to input packets (connection requests, for example) in the manner of an application, while blocking other packets. A proxy server is a gateway from one network to another for a specific network application, in the sense that it functions as a proxy on behalf of the network user.
Proxies make tampering with an internal system from the external network more difficult and misuse of one internal system would not necessarily cause a security breach exploitable from outside the firewall.
Free Third party Firewalls
- Online Armor Free
- Comodo Internet Security
- Outpost Firewall Free
Paid Third party Firewalls
- Comodo Internet Security Pro
- Agnitum Outpost Pro Firewall
- Kaspersky Internet Security
Note
In today’s world the malwares are getting very sophisticated and powerful and can easily bypass strong firewalls that are setup in any organizations. So extra care needs to be taken to secure the organization’s networks. As a saying goes “Better safe than sorry”, in IT world its “Better secure than sorry”.
Reference links:
- http://en.wikipedia.org/wiki/Firewall_%28computing%29
- https://www.cs.columbia.edu/~smb/classes/f06/l15.pdf
- http://personal-firewall-software-review.toptenreviews.com/